Shop Noise-Canceling Headphones – Details and More
Shop Noise-Canceling Headphones – Noise-cancellation headphones decrease or remove unwanted ambient sounds. It’ll be reached in several ways, but the…
Sole Proprietorship Business Examples: Real-World Businesses You Can Start Today
When you have ever run a small store, worked online as a freelancer, baked cakes to sell them, or provided…
Business Analyst Resume: Skills, Experience & Winning Format
A resume of a business analyst is not a list of tools and credentials and former job titles. It is…
Business Pitch: A Comprehensive Research Guide
Business Pitch – A properly developed pitch can be the key to receiving a funding in the modern business world…
Ponds White Beauty Serum Cream – Benefits, Tips And More
Ponds White Beauty Serum Cream – Do you want one product to do all this and make your skin tone appear…
How to Lose Arm Fat? – Details and More
How to Lose Arm Fat? – Arm fat is extra skin and fat situated under your arms. However, it’s not…
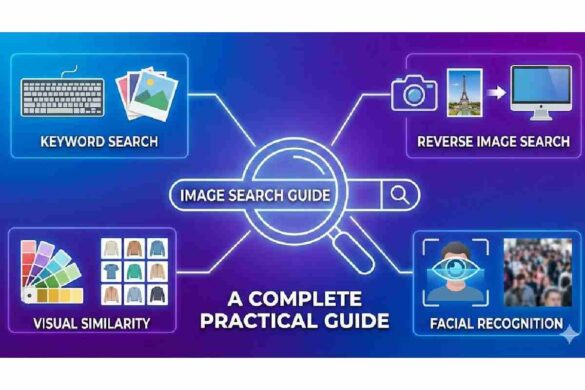
Image Search Techniques: A Comprehensive Research Guide
Image search techniques are the techniques and technologies of locating pertinent images within a large digital repositories on either of…
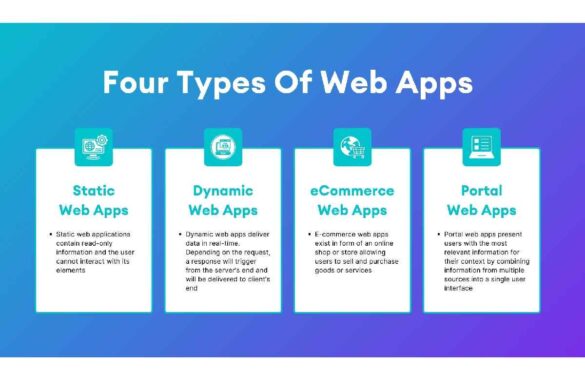
Web App Ideas – Information And More
Web App Ideas: With the digitization in modern life, many people are accessing smartphones to manage nearly every task. In…